Highlights
Rapid analysis
Disasm & decompile
Malcat also embedds the Sleigh decompiler for x86 and x64.
Embedded files
Smart visualization
Compare binaries
Kesakode database
Advanced editing
Dealing with encrypted or encoded content? Just select the data and chose between dozens of decryption and decoding algorithms.
Known patterns
Extract strings
Strings are then weighted and sorted by score to give you the most pertinent results first.
Powerful UI
Want to go fast? You can navigate through the analysis using numerous keyboard shortcuts.
Make it your own
You can create new file type parsers, decryption routines or add new anomalies with ease.
Latest articles

Malcat tip: fast unpacking of RTF payloads
2024/08/10In this short tutorial, we will see how to extract binary payloads from RTF documents using Malcat. We will then proceed to emulate a shellcode for CVE-2017-11882 and extract the download link.
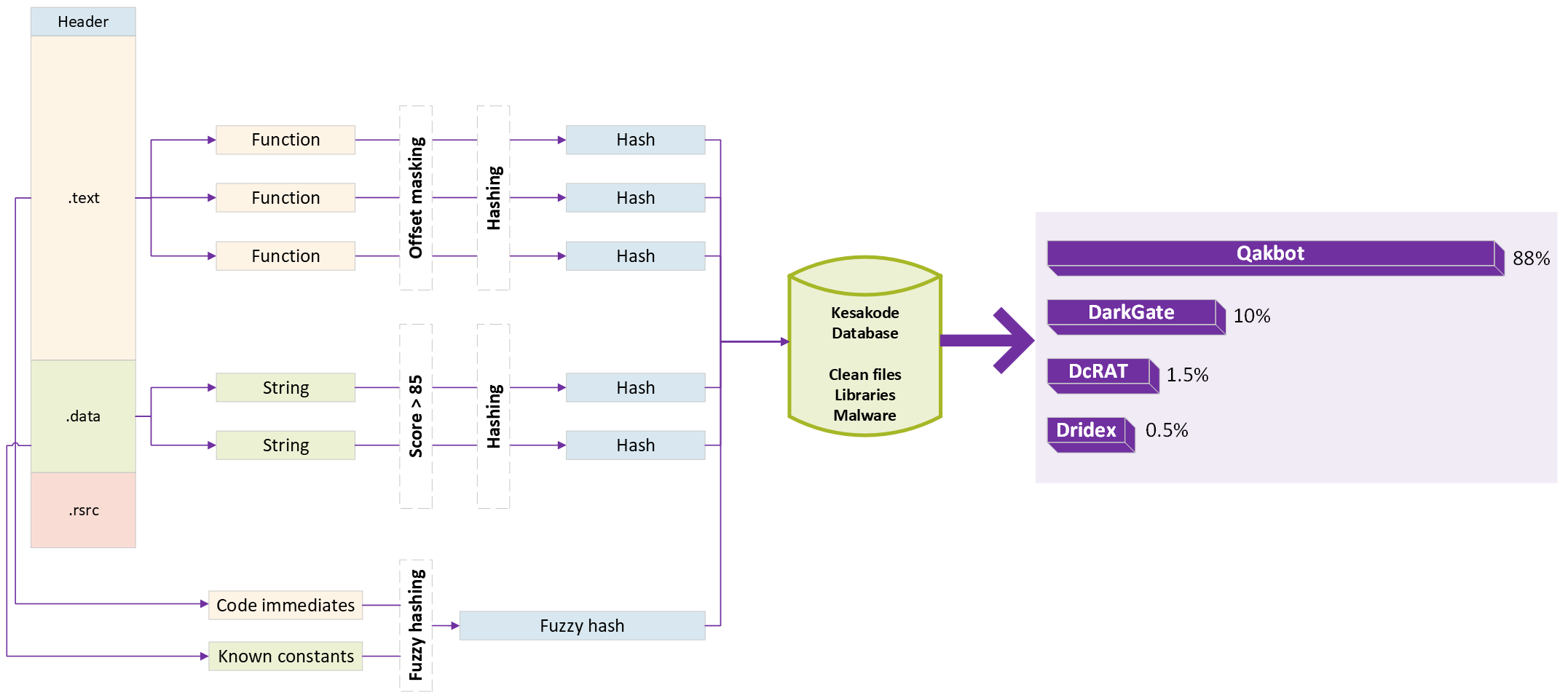
0.9.6 is out: Kesakode malware identification!
2024/05/26Malcat version 0.9.6 is out! We have launched our brand-new online hash lookup service: Kesakode. You'll be able to identify (unpacked) malware, see similarities between malware families, write better Yara rules and speed up your reverse engineering game!
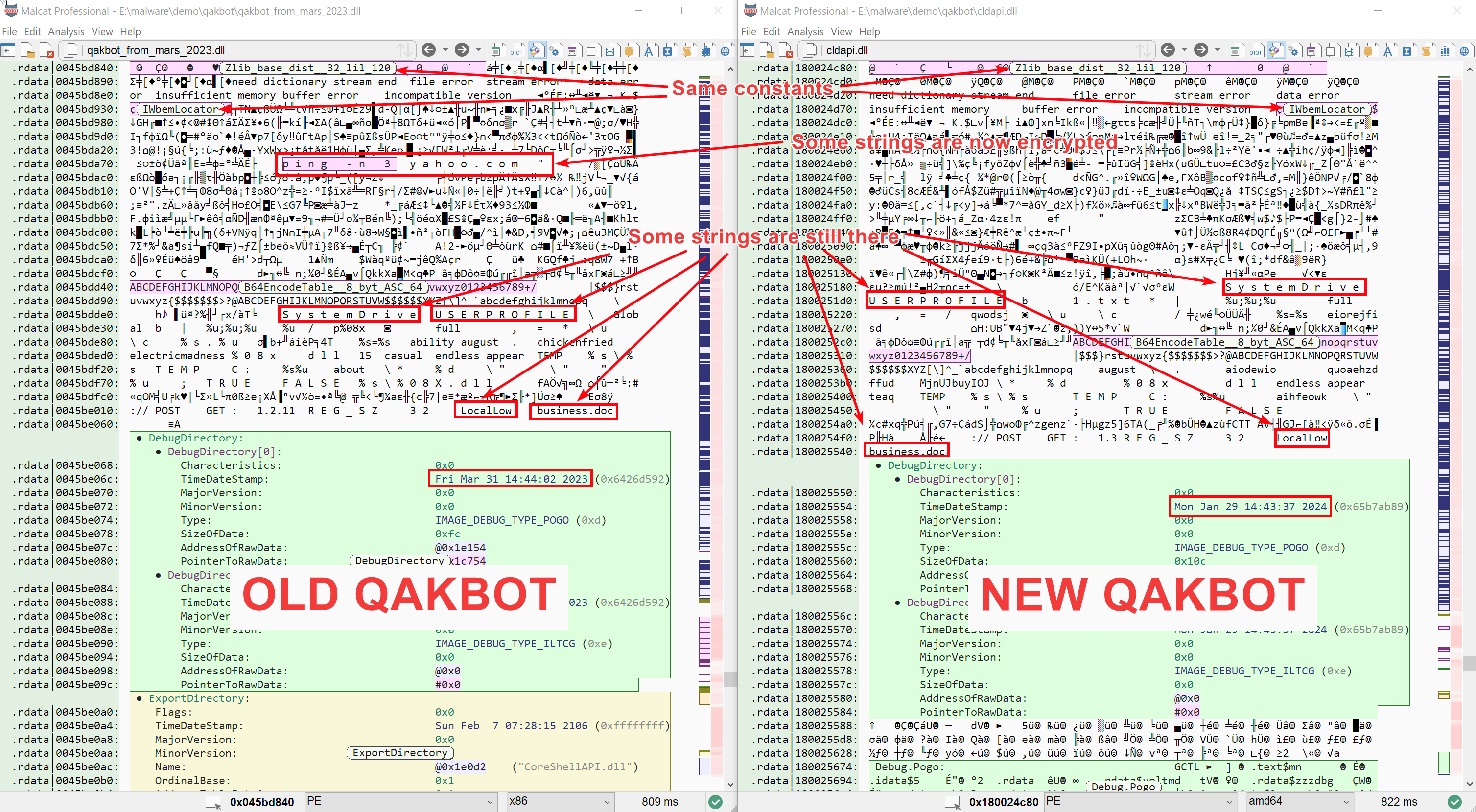
Writing a Qakbot 5.0 config extractor with Malcat
2024/02/16Starting from a (backdoored) MSI installer, we will unroll the infection to chain to get the final Qakbot sample. Sticking to pure static analysis, we will then decrypt Qakbot's configuration and finally write a script in Malcat to automate the process.
Get the software
- Malcat Lite is a free (as in free food) edition with some limitations
- Malcat is the full version of the tool, affordable for hobbyists
- Malcat Pro is targeted toward computer infosec professionals. It allows commercial use and comes with support
Paid version gives you access to unlimited use of the software on Linux and Windows platforms, and access to product updates for one year. Licenses are user-locked and allow installation on up to 5 different machines. If you are not sure if the software can run on your configuration, please test with the free lite edition first.
| Malcat Lite | Malcat | Malcat Pro | |
|---|---|---|---|
| Unlimited use + 1 year of updates | – | ||
| Updates renewal (1 year) | – | 39€* | 179€* |
| Hexadecimal editor | |||
| File format parsers Inspect more than 50 binary file formats |
|||
| Transforms Decrypt/decompress data in-place |
|||
| Signature scanner + editor Scan for constants + yara signatures and edit Yara rules |
|||
| Strings and symbols Powerful strings and symbols (FLIRT) identification |
|||
| Sub-files extraction Explore archives and embedded files |
|||
| Scripting Automate analysis or run scripts |
|||
| Disassemblers Disassemble different CPU architectures |
x86/x64 only | ||
| Decompiler View source for x86/x64, AutoIT, MSI and Office |
– | ||
| Diff engine Compare binaries using Myers algorithm |
– | ||
| Anomaly scanner Quickly identify suspicious files |
– | ||
| Threat intelligence Search local and online datasets |
– | ||
| Python headless mode Analyse files directly from python, no GUI needed |
– | ||
| Kesakode access Identify malware based on multiple artifacts |
– | 40 queries / month | 80 queries / month |
| Support | – | best effort | |
| Commercial use | – | – | |
| Download | Buy for 49€ | Buy for 199€ |
*: Additional taxes may be added in some regions and are calculated automatically during checkout by our payment provider.
Frequently Asked Questions
Reverse engineers have a lot of options nowadays when it comes to analysing known software: IDA, Binary Ninja, Ghidra and many more. So one may ask: was another binary analysis software really needed?
IDA-like tools are basically made to answer one big question: how does a given binary software work? And they are really good at it, provided you plan to spend several hours digging in the same binary.
Malware analysts, incident responders and SOC analysts on the other hand have to analyse and triage large amounts of unknown binaries in a short time span. When opening a file, they do not care as much for the how as for the what. They want to know what is the file they are looking at and what it contains. And because malware are tricky, they have to answer this question for a lot of different file types (installers, archives, office documents, programs, ...) and architectures (NSIS, AutoIT, .NET, python, x86/64, ...). And this is a different problematic, different enough to justify the need for another class of tool.
Until now, malware analysts had to rely on either outdated tools (like the excellent Hiew) or on a lot of different utilities, each addressing a small subset of the problem. Malcat tries to combine all the features of these utilities in a single, powerful user interface. So yes, Malcat also embeds a disassembler and a decompiler like IDA, but the similarity ends there: they are two different types of tool which play in different categories.
If you purchase a license, you may run the software for an unlimited period of time. You only get updates for one year though. After this period of one year, you may still run the software, but won't be able to get new updates until you renew your license.
You don't have to renew the license every year though, you may chose to renew your license at the time of your choice (even long after the 1 year threshold) and you will always benefit of the low license renewal price (50%). We don't want to milk users every year. It's up to us to convince you that Malcat's improvements are worth it.
- Non-commercial usage: You are a network administrator at a commercial organization with discretionary budget and have been practicing CTF on your own time using work resources (approved by work). Your usage qualifies for non-commercial use as you are using Malcat purely for educational, non-commercial purposes.
- Commercial usage: You are a network administrator at a non-profit or government organization who regularly engages in malware analysis as a part of your job. You plan to use Malcat to analyze malware during paid work-hours. Your use is commercial.
If you own a named license, which is the case if you bought it from this website, the license is bound to you and only you. As stipulated in the EULA, it means that you cannot rent or make the software available to other users. This includes the integration of the python module into any user-facing program and/or service. Here are some examples of what you may or may not do with your personal license:
- OK: You are a SOC analyst. You've made a script to assist you in your job which automatically updates your incident tickets with information coming from Malcat. This fits within the bounds of a named license.
- Not OK: You are a SOC analyst. You've made a script that automatically updates all incident tickets of your SOC with information coming from Malcat and integrated it in the SOC stack of your company. This is assimilated to sharing the software with other users.
- OK: You are a security/academical researcher and used Malcat's python module and its CFG reconstruction to analyse large batch of files and do machine-learning detection. You have published the result of your research online. This all fits within the bounds of a named license.
- Not OK: You are a security/academical researcher and used Malcat's python module and its CFG reconstruction to analyse large batch of files and do machine-learning detection. You have additionally made a online service where users can scan their files online using your technology. This also assimilated to sharing the software with other users.
No trick there, this is merely common sense. If you want to integrate Malcat in a multi-user software and/or online service, you can contact us and we will work a OEM license out. Don't worry, chances are it will be much cheaper than the concurrence.^








